The primary usage of wireshark is to visualize packets coming from traditional IP traffic, that is why default wireshark settings provides a relatively good overview of IP packets for most of the use cases.
The problem is that this configuration is not at all suitable for specific needs of Telecom traffic analysis, and does not give you a quick vision when you are working on an SS7 Pcap.
Here is an example of SS7 traffic using default wireshark settings:

With default wireshark configuration:
- You cannot see the interesting addresses in packet list view due to different addressing in SS7 and multiple layers involved.
- You see only one color for all different SS7 traffic types, because wireshark pre-configures coloring only for standard protocols.
Why SS7 traffic is more complex to analyze
First, SS7 Addressing is more complex than IP :
Instead of only IP + port tuples to represent endpoints of IP communication, in SS7 you use Global Titles (GT), Point Codes (PC or SPC) and Sub-System Numbers (SSN), that can be used as follow:
- Global Title (GT)
- Global Title + Sub-System Number (GT + SSN)
- Point Code (PC)
- Point Code + Sub-System Number (PC + SSN)
- Sub-System Number (SSN)
Secondly, their are much more network layers involved in Telecom traffic than on usual IP only traffic. On typical SS7 traffic you face in order:
- Ethernet
- Multiprotocol Label Switching (MPLS)
- Internet Protocol (IP)
- Stream Control Transmission Protocol (SCTP)
- MTP Level 3 (MTP3) User Adaptation Layer (M3UA)
- Signalling Connection Control Part (SCCP)
- Transaction Capabilities Application Part (TCAP)
- Mobile Application Part (MAP)
Each of these layer contains more parameters compared to IP.
Besides, many small packet flags are critically important, such as M3UA Network Indicator (Coded on 1 Byte, it represents the type of SS7 link : Internal, National or International).
CUSTOMIZE YOUR WIRESHARK
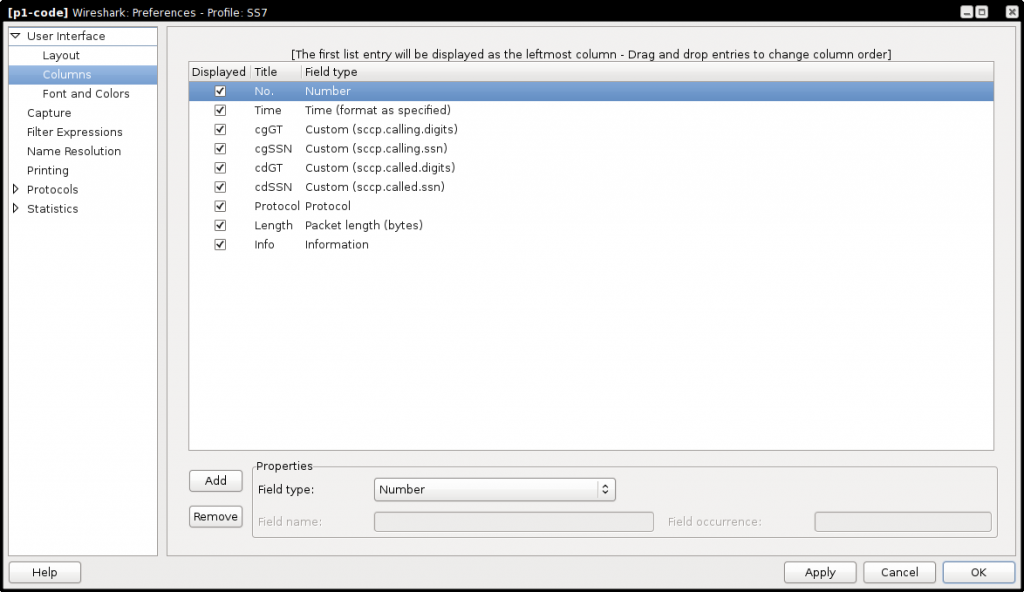
Customize Wireshark columns
You can customize the display columns of Wireshark to show GT and SSN in the packet list view, and do this in a separate profile to have different views on your packet depending of your activity.

How to configure column display (wireshark >= 1.8.0)
- Create a new profile : Go to “Edit > Configuration Profiles”, click on Add and call it “SS7″.
- Add a column: Right click on the packet list view column titles and go in “Column Preferences”. In this window, click on “Add” to add a column, and set it’s name by clicking on it in the columns list.
- Set the field type in the “Field Type” of your new column, select “Custom”. Now you can enter your wireshark expression in “Field Name”, for example sccp.calling.digits or sccp.called.ssn.
- Click on “Apply”: you will have your new column in your Wireshark packet list view.
NOTE: This can be generalized to any Wireshark expression, so you can display any data you want from the pcap in the columns view.
Exporting / Importing columns setting
The following file stores the configuration for your Wireshark profile:
/home/user/.wireshark./profiles/SS7/preferences
Example:
Customize Wireshark coloring rules
To get a better overview of the SS7 traffic and identify types of messages just by looking quickly at them, you can customize wireshark coloring rules. Each rule is defined by one filter (using the same syntax as usual wireshark display filters), and a set of 2 colors (foreground and background colors).
Here is an overview of 4 basic coloring rules applied on typical SS7 traffic:

On the above screenshot, MAP layer is identified by yellow or green background color, whether the message is a MAP invoke (request) or MAP returnResultLast (answer).TCAP Abort (cancellation of TCAP dialog due to error) has a pink background, and TCAP Begin (initialization of TCAP dialog) has a light blue background (Not visible on the screenshot).
How to configure coloring rules (wireshark >= 1.8.0)
- Go to “View > Coloring Rules”.
- Click on “New” to add a new rule.
- Enter a wireshark display filter in “String:” text box. For example, to match MAP invoke messages you can use the filter “gsm_map.old.Component == 1″.
- Choose one foreground and one background color for this filter, then click “OK”
NOTE: coloring rules will be tried in order until one filter matches, top filter having the highest priority.

Exporting / Importing coloring rules
- Go to “View > Coloring Rules”.
- Optional: select one or more filtering rules to export by clicking on them. (Ctrl + Click to select multiple filters).
- Click on “Export”.
- Choose an output filename and optionally check the box “Export only selected filters”.
You will get a file # DO NOT EDIT THIS FILE! It was created by Wireshark
@MAP ReturnResultLast@gsm_map.old.Component == 2@[61023,65535,29648][0,0,0]
@MAP Invoke@gsm_map.old.Component == 1@[37006,53439,22070][0,0,0]
@TCAP abort@tcap.abort@[65535,52907,60113][0,0,0]
@TCAP begin@tcap.begin@[36382,59634,65535][0,0,0]
This file can then be used to import coloring rules on another host.
That’s it ! Don’t hesitate to comment with you’re own Wireshark tricks.
In a future blogpost, we’ll see how to use Wireshark to edit a PCAP, in order to forge packets or anonimize a PCAP file.




